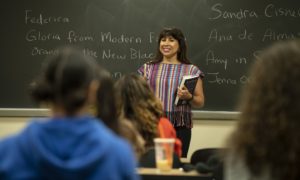By Tracey Lien
Los Angeles Times
WWR Article Summary (tl;dr) A group of Stanford students are trying to solve some of the toughest problems facing the country and the world. In courses like “Hacking 4 Defense” and “Hacking 4 Diplomacy”, teams of students choose from a list of real problems plaguing the government. The teams are then paired with sponsors from the Defense or State departments and tasked with not just finding a solution, but coming up with a viable product that the government would actually use.
SAN FRANCISCO
They’re some of the brightest students in the country, a group of wunderkinds known for hacking their way through any problem thrown at them. So what could possibly stump a Stanford University student?
Government bureaucracy, it seems.
In a lecture hall nestled in Stanford’s Environment and Energy building, dozens of engineering, science and arts students were put through the bureaucratic wringer this year when they took Hacking 4 Defense and Hacking 4 Diplomacy.
The courses, taken for credit and taught by Stanford instructors, let teams of students choose from a list of real problems plaguing the government, paired them with sponsors from the Defense or State departments, and tasked them with not just finding a solution, but coming up with a viable product that the government would actually use.
“It was really humbling,” said Katie Joseff, 21, a human biology major who took Hacking 4 Diplomacy this fall. “My team had to make lots of pivots because over and over again our assumptions just weren’t correct. We had to first break through the bubble of Stanford, then Silicon Valley, then California, then the U.S.”
The problems included finding ways to track objects in orbit to prevent space collisions, developing tools to assess the effectiveness of peacekeeping forces, and in Joseff’s case, designing a platform for a coordinated response to the Syrian refugee crisis.
Like many students, Joseff went in thinking there would be an easy technological fix: Perhaps an app that would enable nongovernmental organizations to communicate with refugees, or a platform on which NGOs could share information with each other, or another app through which refugees could send feedback to NGOs.
But after interviewing more than 100 people in the sector, she realized that apps aren’t the answer to everything. In fact, some 200 apps had already been developed to help with the refugee crisis, and only two of them were in use.
With each interview, Joseff’s team learned that many NGOs already had ways of reaching refugees, they didn’t need another app.
They also learned that NGOs are reluctant to share information on a platform because so much of their data is sensitive. And if refugees had a way of sending NGOs feedback, who exactly would that information go to? Was there even enough personnel to handle the information?
“People are obsessed with hacks and hackathons, and they think they can solve these issues with technology,” Joseff said. “But we learned that the human element is still needed.”
The classes come at a time when Washington is trying to forge deeper connections with Silicon Valley, with the hope that the region’s tech-savvy and innovative streak will rub off on government agencies.
The Department of Defense opened its Defense Innovation Unit in Mountain View, Google’s stomping ground, last August.
The State Department created the role of ambassador to Silicon Valley this year and appointed the director of its Strategy Lab, Zvika Krieger, to the post (Krieger teaches Hacking 4 Diplomacy alongside Stanford professors).
The Department of Homeland Security recently held a meeting with local tech startups to offer funding to companies developing technologies that the department can use. And earlier this year the Obama administration invited representatives from Silicon Valley’s top firms to Washington to brainstorm ways to fight the militant group Islamic State online.
“So much of what we’re doing is at the intersection of policy and technology,” said Deputy Secretary of State Tony Blinken, who visited the Hacking 4 Diplomacy class in November. “At the same time, many of us don’t have the background and expertise when it comes to tech. We need technologists and innovators in the room just to tell us whether we need technologists and innovators in the room.”
Stanford University has a reputation for being a breeding ground for technological innovators, counting among its alumni founders and executives of Google, Yahoo, PayPal, Netflix, LinkedIn and Instagram. Long synonymous with Silicon Valley, the university is often the first stop for tech firms looking for engineering talent, and the place where hot companies such as Snapchat got their start.
Class instructors admit there was some trepidation over how Hacking 4 Defense and Hacking 4 Diplomacy might be received by students, given the school’s history as a hub for private-sector tech, and the general distrust between Silicon Valley and the federal government. Leaks by former National Security Agency contractor Edward Snowden and the high-stakes encryption fight between the FBI and Apple have heightened longstanding tensions between two vastly different cultures, which both believe they know what’s better for the world.
But they were surprised to learn that, far from being cynical, students were drawn to the opportunity to solve some of the toughest problems facing the country and the world.
Over 10 weeks, students in each class wrapped their heads around the bureaucratic workings of the Defense or State departments, interviewed at least 10 stakeholders a week, and learned the Lean LaunchPad method, an approach to startups and entrepreneurship that helps company founders identify markets for their products.
For many, it was the first time they’d used the skills learned in school to tackle real-world problems. And nearly all butted up against challenges that technology alone couldn’t fix, and were forced to throw out their ideas again and again.
Zvika Krieger, center, an instructor of Hacking 4 Diplomacy at Stanford University, speaks to students during one of the final classes of the semester.
“They all think they’re the smartest kids on the face of the earth, and they kind of are,” said Steve Blank, creator for the Lean LaunchPad method and adjunct professor at Stanford who co-taught both classes. “That’s why it’s so much fun to watch them get smacked down by reality.”
In Hacking 4 Defense, students also bumped up against the realities of global problems.
Rachel Olney, a 23-year-old mechanical engineering masters student who took the class in spring, was part of a team that was tasked with creating a sensor to help Navy divers monitor their physical health while underwater.
“We thought, ‘We can do this, this is an engineering problem,'” she said. “We were thinking about casting sensors into rigidified silicone, or we were going to build this app and it would be wonderful.”
But when she pitched this to Navy divers, they were put off by the idea of wearing sensors that would track their movement.
After dozens of interviews, her team realized the reason divers needed sensors to begin with was because every time they moved from deep water to shallower depths, which they had to do to get their GPS location, the “decompression” put stress on their bodies.
“So we realized if we could reduce the number of decompressions divers do, we’d be solving the health problem, and they wouldn’t need a wearable sensor,” Olney said.
Olney’s team mocked up manufacturing specs for GPS buoys that divers could deploy below the water on their behalf, and they built a prototype of the product, too. Not all teams get as far, which is fine, Blank said. The class isn’t a startup incubator, or a government internship, or even a recruitment drive for the Defense and State departments (although government sponsors hope it will open students’ eyes to careers outside of Silicon Valley).
The entire class is open source, which means anyone can use or build on what the students come up with. Students are expected to have a minimum viable product they can get into the hands of potential users. But the bulk of their grade is based on how well they applied the Lean LaunchPad methodology to their problems.
Hacking 4 Defense has already been green-lit at Stanford for next quarter, and the class will next year expand to the University of California, San Diego, the University of Pittsburgh, Georgetown University and James Madison University.
Its diplomacy counterpart is wrapping this month, and the school and State Department will evaluate its success after final student presentations.
Joseff and her team ultimately decided to work on a tool that would let refugees self-govern (although they ran out of time during the 10-week course to develop it). She isn’t sure if she will continue to develop her team’s products once the class ends, nor does she know if she wants to work for the government. But the class has been a “jolt” for her.
“It’s refreshing,” she said. “Being in Silicon Valley, a lot of my friends want to go to Google or Apple, but this class shows people they can also work in public service. I used to watch the news about Syrian refugees and feel paralyzed and hopeless. But this class has helped me realize I can have a bigger impact.”