By Omri Lavie
Globes, Tel Aviv, Israel
WWR Article Summary (tl;dr) Omri Lavie takes a look as some of the key issues that the cybersecurity industry needs to confront in the age of Coronavirus.
Tel Aviv
The unprecedented spread of Covid-19 worldwide, which is still growing, has brought about changes in many day-to-day activities. We have shifted from face-to-face to virtual, online meetings, we have switched from visiting our family doctor to consulting with them via an app, we’ve traded our runs in the park for working out in front of a screen, and our kids now “go to school” on the dining room table via Zoom.
In an incredibly short amount of time, we’ve understood that almost anything could be easily done remotely, from anywhere, using our computer or mobile phone.
This trend expanded the traditional boundaries of the cybersecurity industry, an industry whose solutions secure almost every online process.
The way in which this industry will change after the Covid-19 crisis poses a challenge that intrigues many tech entrepreneurs. These are some of the key issues that the industry needs to confront.
Personal tracking technologies: These technologies have recently become an important tool in preventing the spread of Covid-19. For example, the global video tracking market, worth $50 billion in 2020, is expected to grow to $75 billion in 2025. The campaign against gathering information on the individual, and the controversy about the extent to which these technologies violate privacy, have somewhat slowed down their adoption, but the COVID-19 pandemic has proven their dramatic importance in preventing the spread of the virus.
For example, the Governments of South Korea, India and Israel have begun using technologies for tracking mobile phones in order to locate people infected with the virus. In the business sector, Google developed the Covid-19 Tracker app, which uses location data of cellular phones in order to analyze change in movement patterns within certain communities since the virus pandemic began. Google is also collaborating with Apple in this field, showing that the two leading manufacturers of smartphone operating systems have played their part in dealing with the problem.
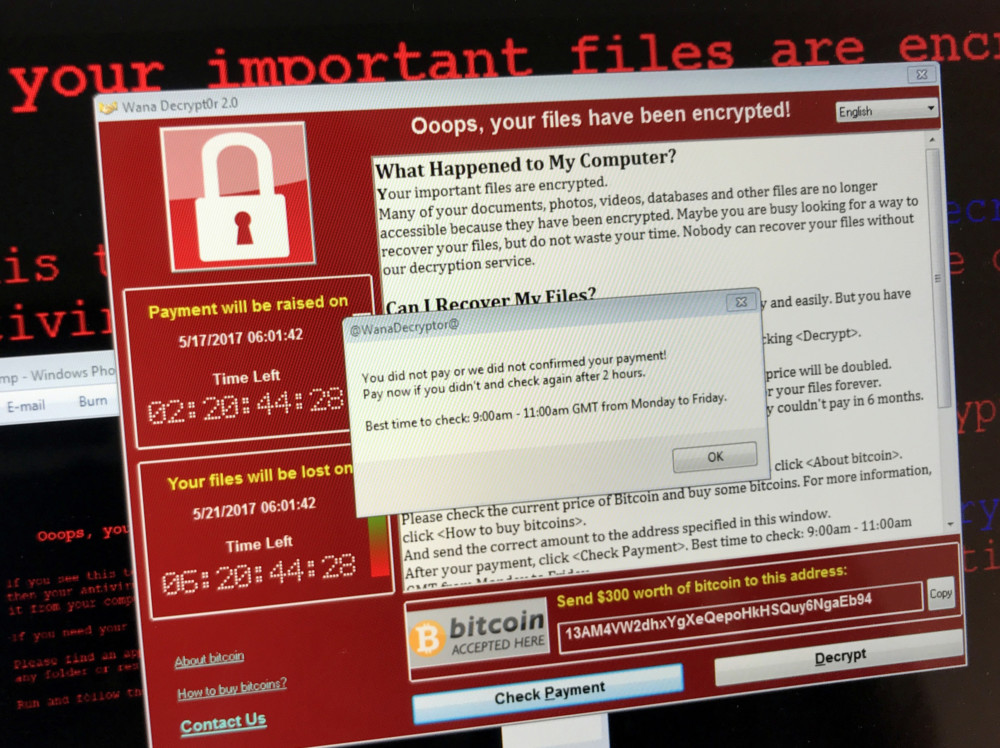
The work environment and remote learning: Cyberattacks were always an integral part of the online footprint. However, the volume and frequency of cyberattacks has risen significantly following the changes that the pandemic created in the way we conduct our personal and professional lives. These changes have generated a necessary shift from a secure work environment in the office to a remote working environment that, for the most part, is not secured as it should be. Our personal computers are typically not “wrapped” in a sealed envelope of enterprise security like the ones in the office, and have therefore become an attractive security breach for hackers. Consequently, we need to further grow and develop enterprise awareness and organizational responsibility to protect the remote working environment in the same manner we protect the office and other work environments.
But a cardinal problem has emerged. Unlike in office work environments, home users tend to avoid using cumbersome security software that is not user-friendly and often resource-heavy. Consequently, as a general rule, the online home (remote) work environment is not adequately secured. Many organizations are becoming aware of this threat and have grown their investment in security software that is adapted to remote work.
In addition, we see bigger investments in training and guidance to employees on ways to prevent and cope with security breaches in the remote work environment.
buy kamagra soft online pridedentaloffice.com/wp-content/themes/twentytwentyone/inc/en/kamagra-soft.html no prescription
It should also be mentioned that organizations will be required to apply stricter, more rigorous cyber security policies to allow remote but secure access to their work servers. Without hardening these policies, organizations will be exposed to attacks that originate mainly not from the secured enterprise network but from the remote work environments.
Simple from home, simple in the organization: The need to simplify the use of remote work environment protection tools, along with the application of more rigorous cyber security policies, is likely to exacerbate one of the main challenges the industry is currently facing: lack of compatibility between the broad range of security solutions that are used in defense of the home and office work environments. These solutions are not only incompatible with one-another, but also often clash and become liabilities rather than assets to the organization. Consequently, there is a need to move away from reliance on collections of individual solutions to adoption of cross-lateral security platforms, which combine a range of different tools working in full synchronization. Such platforms unify different and separate security solutions to provide a raft of tools that are not only useful in the defense of organization but also simplify the application in both the office and the remote work environments.
Lastly, and probably most obviously, the cybersecurity industry is challenged anew every single day by hackers (“puzzle solvers”) who are attempting to breach the security walls that are built around the data and information of each and every one of us. That, along with the other challenges that the Covid-19 pandemic has brought to our online presence, has created a new range of needs with which the industry will comply. Organizations that will choose to ignore these changes will quickly face the key law of evolution: ‘evolve or die’.
The author is a cybersecurity entrepreneur, CEO of Orchestra and a cofounder of NSO Group
___
Distributed by Tribune Content Agency, LLC.